Critical Security Flaw in PaperCut Software: What You Need to Know
Written on
Chapter 1: Overview of the PaperCut Vulnerability
A significant security threat has emerged, centered around the PaperCut software suite, affecting document management systems used by approximately 70,000 organizations globally. The FBI and the Cybersecurity and Infrastructure Security Agency (CISA) have issued a joint report detailing a critical vulnerability, designated CVE-2023–27350, which is currently being exploited by various cybercriminal groups and state-sponsored actors.
"This vulnerability poses a serious risk to organizations relying on PaperCut MF and NG."
Section 1.1: Exploitation Methods
The FBI and CISA have identified two known methods demonstrating how malicious code can be executed in the vulnerable PaperCut applications. The first method involves the use of the print scripting interface to run shell commands, while the second exploits the user/group synchronization interface to facilitate a "living-off-the-land" attack. This approach utilizes legitimate software functionalities to conduct harmful activities.
Subsection 1.1.1: Elevated Privileges

The recent vulnerability allows attackers to bypass authentication measures and execute arbitrary code with SYSTEM privileges. The pc-app.exe file, which operates on affected PaperCut servers, has elevated permissions that can be exploited to run additional processes, such as cmd.exe or PowerShell scripts, thereby granting attackers extensive control over the server.
Section 1.2: Urgent Response Required
In March 2023, PaperCut acknowledged this vulnerability and updated its website to alert users about the ongoing threat to unpatched servers. An urgent notice prominently displayed on the site is directed at all users of PaperCut MF and NG.
Chapter 2: The Impact of Ransomware
The first video titled "Hunting for PaperCut RCE Exploitation (CVE-2023-27350)" explores the implications of this critical vulnerability and the various tactics employed by attackers.
The Bl00dy Ransomware Gang has been particularly aggressive, leaving ransom notes on compromised systems and demanding payment for file decryption.
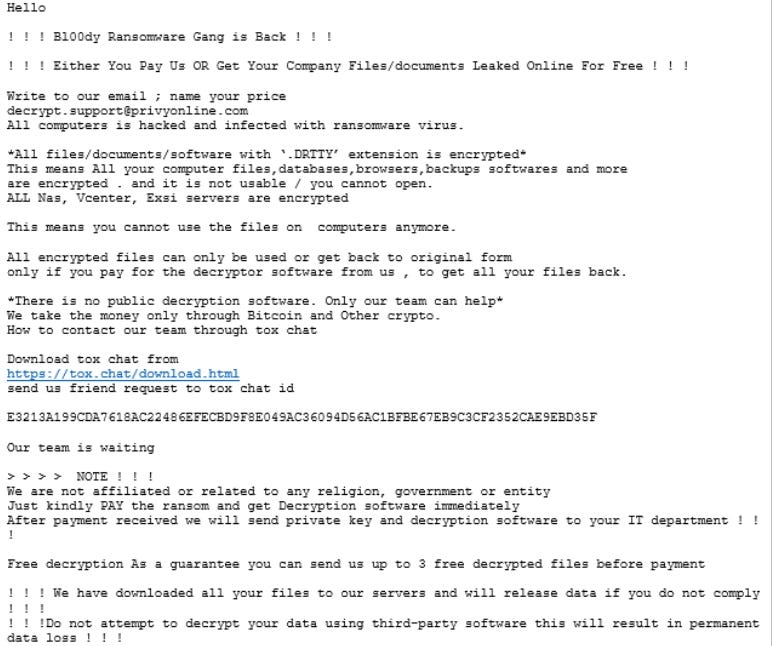
Section 2.1: Additional Vulnerabilities
Another vulnerability, identified as CVE-2023–27351, also affects PaperCut MF and NG. This flaw enables unauthorized access to sensitive information, including usernames, email addresses, and associated card details.
With over 70,000 organizations utilizing PaperCut across more than 200 countries, the potential for exploitation has gained the attention of malicious actors. Notably, around 68% of exposed PaperCut servers in the United States are linked to educational institutions, though the software serves a diverse clientele, including government entities, healthcare, and legal sectors.
Chapter 3: Detection and Mitigation Strategies
The second video titled "CISA Alert AA23-131A – Malicious Actors Exploit CVE-2023-27350 in PaperCut MF and NG" outlines the steps organizations should take to detect and mitigate threats associated with this vulnerability.
To effectively combat this cybersecurity threat, CISA recommends several strategies. IT teams should closely monitor network traffic directed at the SetupCompleted page of any exposed PaperCut server. CISA has provided a Proofpoint Emerging Threat Suricata Signature to assist in identifying such activities.
Section 3.1: Monitoring for Compromise
It is crucial to track any alterations made by the administrator to configuration keys such as print.script.sandboxed or device.script.sandboxed, as these changes may indicate a compromise. Searching DNS logs for domains linked to recent PaperCut exploitation is also advisable.
Attention should be paid to child processes initiated by the pc-app.exe process, as these may signal a successful breach, especially if they involve known post-exploitation tools like cmd.exe or PowerShell.
Chapter 4: Essential Protection Measures
To protect against potential exploits of the CVE-2023–27350 vulnerability, it is vital to patch affected PaperCut servers promptly. If immediate updates are not possible, restricting internet access to these servers is critical.
Implementing inbound traffic restrictions is an effective method to block external IP addresses from accessing the default web management ports. Additionally, it is advisable to maintain strict Allow List policies, permitting only trusted IP addresses within your network.
Maintaining up-to-date systems and software is a best practice that significantly reduces the risk of falling victim to common vulnerabilities.
Stay informed with the latest cybersecurity developments by joining my Mailing List.